joranna.ng | March 20th, 2020
Since the introduction of APIs (application programming interfaces) 20 years ago, their presence and contributions remain strong in the business world. Frequently, companies leverage a platform in their business/digital strategy, but incrementally include APIs to explore or expand their existing platform. APIs offer the extensions needed to help address specific use cases. It’s unsurprising that Gartner stated that APIs enable a digital business to work by connecting people, businesses, and things.
The flexibility provided by APIs is incredibly powerful but also presents new challenges. Behind every great app is a complex mesh of APIs working hard to efficiently deliver accurate data to the right person at the right time. Therefore, it’s the responsibility of each API, or collection of APIs, to verify that each request is limited to the data they’re authorized to access.
What comes first? APIs or Security?
Developers love to create and deploy cool apps quickly, but moving fast sometimes results in poor security practices. Consequently, embedding security for APIs is usually an afterthought. To further complicate matters, the security and compliance policies for employees and external parties often differ and are sometimes not even articulated clearly. These factors make developers less motivated to ensure that the initial security protocols are included in their APIs.
Let’s look back at the Facebook 2018 breach when 50 million user accounts were impacted. Attackers potentially had the ability to take over user profiles. The source of this breach began with attackers using Facebook developer APIs to obtain user profile information. As the frequency and severity of cyberattacks increase, it’s prudent for companies to ensure that proper authentication and authorization protocols are deployed in their APIs.
Introducing new API capabilities
As a security-first company, we make it easy for developers to integrate their APIs and leverage OneLogin as the API Gateway for authentication and authorization. We are pleased to announce the general availability (GA) of the following capabilities to our core APIs - App API and API Authorization. These API capabilities enable customers to automate app rollout, as well as authorize access, to their own APIs.
What is the App API?
App API gives customers the ability to automate app rollouts and save the stateful configuration deployed in their OneLogin production account. This is extremely useful for customers with several apps to administer or quickly roll out. The Apps API eliminates the pain and time of app administration by automating the app rollout via API.
It also offers consistency and the ability to replicate deployments between different environments such as the OneLogin Sandbox. What does that mean? IT Admins can now create an app connector in the OneLogin Sandbox, test, and use the App API to export the configuration settings, and when it’s ready, push the new app (with the configured settings) into their production environment.
What is API Authorization?
API Authorization generates access tokens used to authorize requests against an API or API Gateway. Basically, API Authorization allows you to configure OneLogin as an Authorization Server. An Authorization Server authenticates a user and returns an Access Token for authorization access to downstream APIs. These APIs could be self-hosted or provided via an API gateway. This smart API capability allows you to customize the JWT access tokens that are generated after a user authenticates via OpenID Connect (OIDC).
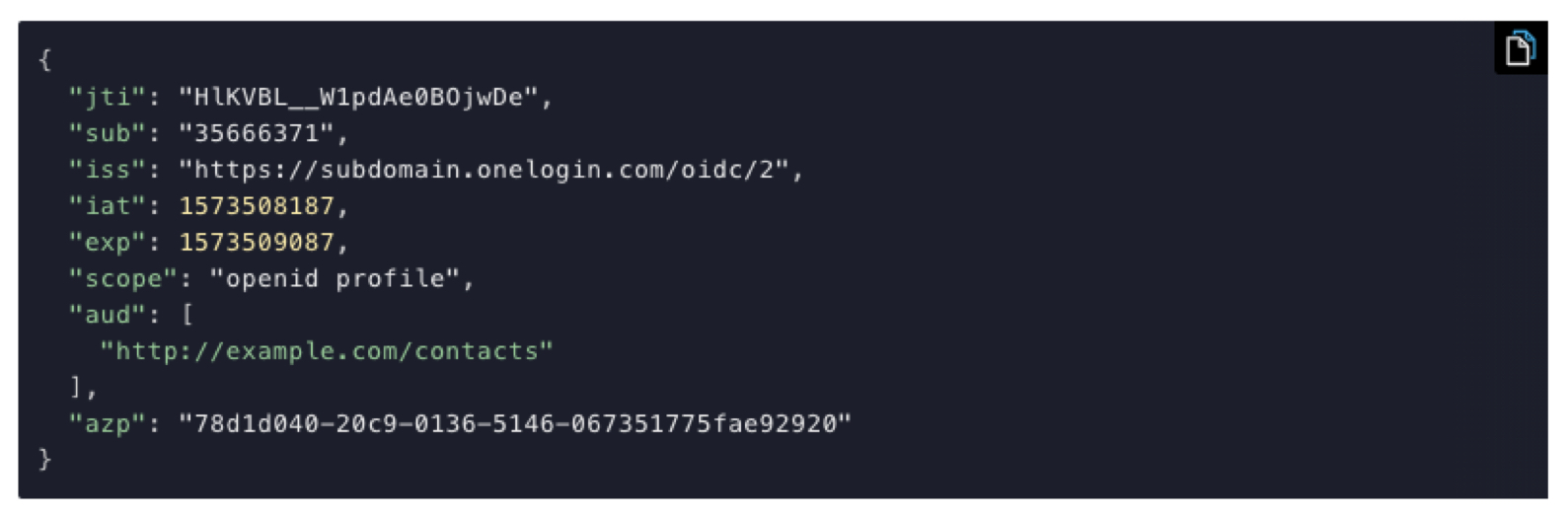
These API endpoints configure the base endpoint of your API, as well as defining scopes, claims, and client apps.
API Authorization includes the following features:
- Resource Identifier & Audience: Every API must have a unique identifier (aka the Resource Identifier).
- Scopes: Used to represent actions or access levels within your API.
- Claims: Attributes that exist in the Access Token - useful for including custom information in the Access Token.
- Client Apps: Because all requests to authorize access to an API must go through an OpenID Connect application, you would need to assign at least one OpenID Connect application to your API Authorization configuration.
Sign up for a free developer account and try out our APIs today!
